After writing a 3 part series on purchasing and using S/MIME certificates with Microsoft Outlook 2016, some months went by I started receiving certificate renewal emails from Entrust. The first encouragement to renew arrived at 90-day warning, then 60, 30 and finally, 10. This post reviews the Entrust renewal process and describes that it is actually a new certificate purchase, not a renewal and describes the configuration changes required to configure Microsoft Outlook to use the “renewal” certificate rather than the expiring certificate.
Review
Recall from part 1 of this series, that the Entrust website requires use of ActiveX controls so it can perform Microsoft Crypto API operations on the Windows PC endpoint where the certificate will be created and installed. More than requiring ActiveX execution on the endpoint, the Entrust ActiveX control is not digitally signed. Together, these mean that Windows is the only operating system and Internet Explorer is the only web browser that will work with Entrust purchasing system and that the IE trusted sites security controls have to be relaxed to perform the purchase. I add that today in January 2017, just as a year ago in 2016, the website still does not “fail early” when you visit in Firefox. You can still get all the way through purchasing and payment and not actually get the private key installed into the certificate store on Windows.
Before you visit the Entrust store to renew certificate, launch internet explorer and temporarily relax the security controls. Details for this are in the part 1 of this series. Quick version:
- Place https://buy.entrust.net on “trusted sites
- Dial security level to “Low” for trusted sites – this permits running non-signed ActiveX controls. Make a note of the before setting and when done, reverse these steps
- These should be put back after completing the certificate purchase/renewal
Renewal process
In IE, browse to https://buy.entrust.net/. Complete the purchase process as in part 1 of this blog series. Receipt will arrive via email. Side note is that the receipt is 10 pages, 1st page is the receipt and 9 that follow are the EULA. When print, save a tree, print only pages 1-1.
A separate email will have the certificate pickup link. This email process is used to validate that the person who is purchasing the email certificate actually has control of the email address. The email contains a web link to continue the CA certificate signature process and this is identical to the original certificate purchase.
In the pickup email, this text
Attention: Be sure to use the same browser to retrieve your certificate that you used to order it. For example, if you used Mozilla Firefox to order the certificate, use Mozilla Firefox, on the same computer, to retrieve it. Do not click the link on a different browser or a different computer. https://www.entrust.net/smime/pickup.cfm?pickupid=123456&tid=12345
Cute! Parts of the Entrust website believe this process works with something other than Internet Explorer. Don’t click the link. Have to copy / paste it into IE which is hopefully still up after the purchase.
OK, done! Not really done. Request for enhancement here for Entrust. You are already running native code on my computer as the presently logged in user. How about walking me through the backup key process and automatically importing the newly purchased key into my email application rather than just having the certificate available in Internet Explorer. This must be done manually and is covered in part 1 of this series.
This is not a certificate renewal
The “renewal” certificate is a completely “new” certificate and the installation process is same to the installation of the “first” certificate a year ago. Entrust “renewal” emails started arriving 90 days before expiration. In my case, I renewed 6 days before expiration of the first year and notice that this caused a loss in validity period of 6 days with a loss in value of 6 / 365 * $20. Yes, this is a cost that I can handle, but it goes to show that the process is not a renewal. Separate certificate issuance and not same day expiration dates drive home the fact that this is a new certificate purchase and there is zero incentive to renew early, or even on-time.
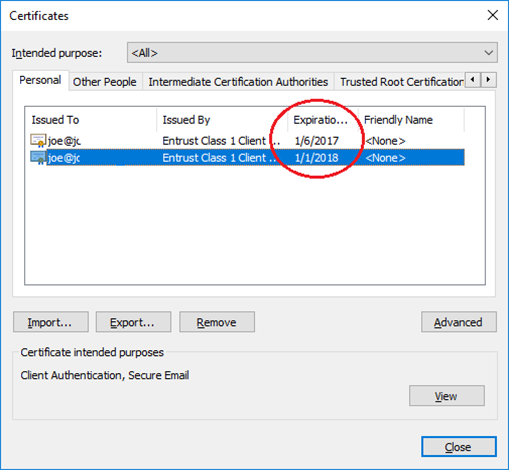
Properly implemented, the “renewal” should change the expiration of the original certificate. That is, the public key of the original certificate should be sent to Entrust to be signed as part of renewal rather than a fresh key. The certificate signing request should denote a 1 year extension of the expiration date – which would fix the disincentive for early renewal.
Notice that in a renewal, the private key should be unchanged, but the key will then have a fresh “attest” that it is legitimate and new expiration date. This is not what happens with Entrust “renewal”, it’s a new key pair and a new certificate on renewal which precisely equals a first-time purchase and there is no alignment of dates.
Security wise, there’s some advantage in generating new keys, but there is a real usability impact of having multiple certificates. It means that to be able to validate signatures on emails sent in the past, the user must maintain ALL of the previous generation certificates. In my case, there are now 2 certificates and next year there will be 3.
Install the certificate for use in Microsoft Outlook
In Outlook 2016, this is Alt-File, Options, Trust Center, Trust Center Settings, Email Security, Digital IDs, Import/Export.
Browse to the key backed up earlier, exported from Internet Explorer (part 1 of this series). Browse to the file holding the certificate with the private key. When import the key you will be prompted to enter the password saved when you exported, and … done. Conceptually done, but not actually done.
Outlook is still using the old certificate
Send a signed email to someone and you’ll see that outlook is still using the “old” certificate. To validate, you must actually send an email to see what was used for the signature. After send, open sent items, open the mail that was sent and then inspect the security of the signature. Multiple screens required to get to this information.
Click the icon, push through a few more screens.
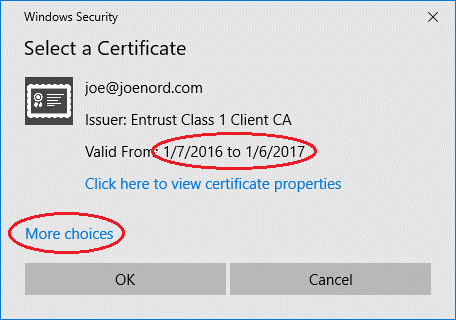
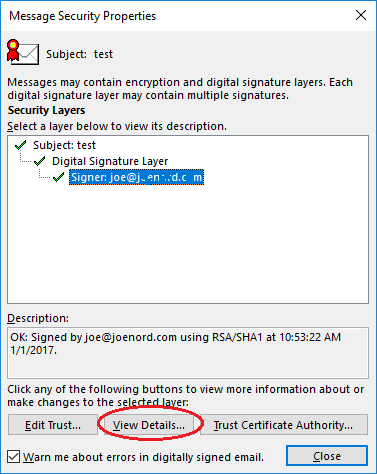
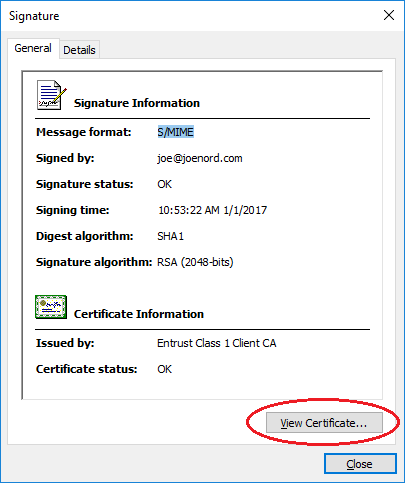
Almost there. When view the certificate we will see that the wrong one was used.
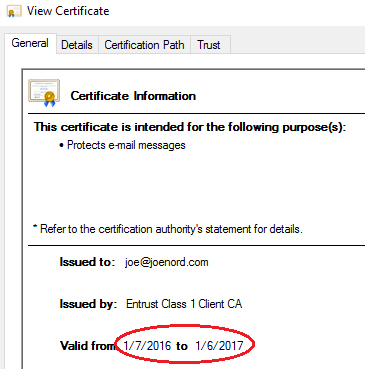
- Outlook is still using the old certificate
- We need to tell it to use the renewal certificate, which is actually a new certificate, but we need to do this without deleting the old certificate
- Yes, that was a whole bunch of steps to verify that this didn’t work
Configure Outlook to use the new certificate
File, Options, Trust Center, Email Security, Encrypted email, Settings, Signing certificate. Below image implies that everything is all set, but it isn’t. You have two certificates (or more) for the same email address and you have to change Outlook configuration to tell it to use the one that was just purchased
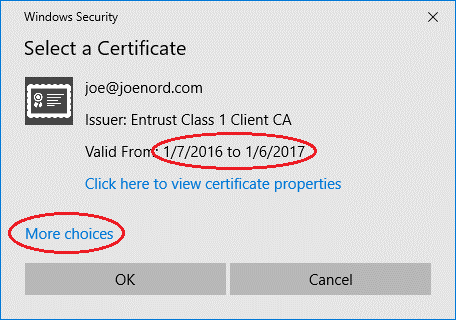
Things to observe
- The default certificate selected is the “old” certificate
- If select “OK”, Outlook 2016 dialog hangs and must be closed
- Selecting “More choices” is the correct thing to do
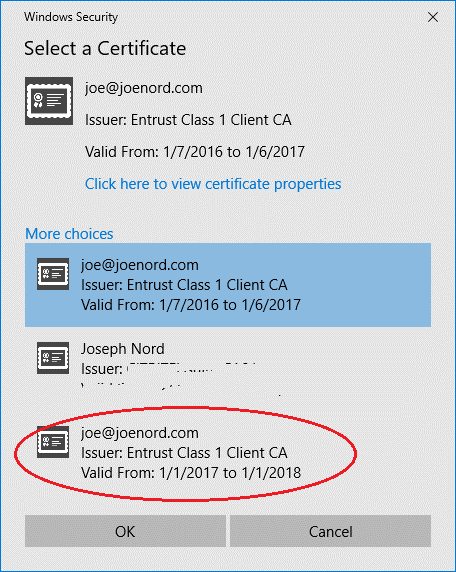
The “default” certificate for this account is the “old”. Select the new certificate and press OK.
Get another dialog to set encryption parameters.
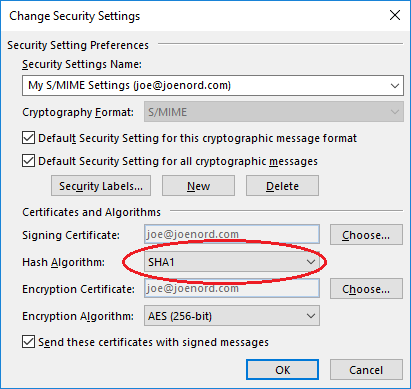
Just like a year ago, the default hash is SHA1 which is depreciated by NIST so should not be used. The people of the world still using a computer with Windows XP before Service Pack 3 will have to upgrade to receive your email. Change the hash to SHA2 / SHA256.
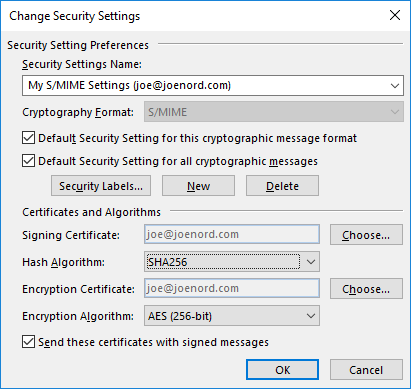
Click OK to close out the set of configuration panels.
Verify it is now working
Send another signed email and this time the new certificate will be used.
Conclusions
It is always fun to go back in time and read “Why Johnny can’t encrypt”. That was written 1999 and today in 2017, this remains true. Users should not be expected to have this level of expertise just to send a secure email, but they still are placed in this situation causing for the most part a complete inability to have secure email on the internet. With work by using parties, it can be accomplished. I hope this small blog assists.
For the Entrust “renewal”, I summarize to
The Entrust email certificate “renewal” is actually a fresh certificate purchase
There is no advantage in renewing early, and indeed there is a a disincentive to renew early
Since renewal is a new certificate, actions must be taken to convince Outlook to use the new certificate rather than the old
Entrust purchasing website expecting ActiveX to be available and browser configured to be willing to run non-signed controls in modern times is hard to justify
A native application is needed! The application should be downloaded and executed to guide the user through the certificate purchase, backup and certificate installation process. While in there, also implement true “renew”
I’m in for another year and this will work. Not ideal, but it will work.
Joe Nord
(Originally published Jan 1 2017)