As a big fan of crypto, it has always rather amazed me that S/MIME hasn’t had more success. We hear many accounts of users cannot handle the certificate management required to make something like PGP or S/MIME work. I have been doing some experiments and have concluded that we got it wrong; we are blaming the user when the right person to blame is ourselves. This post describes the first step of success, what it takes to “get a key”.
S/MIME Encryption key – purchase
The end-goal is S/MIME email. This requires getting an encryption certificate, issued by a provider that has a common root of trust. Commercial certificate authorities (CA) are the answer here as their statements of authenticity will root up to validate trust by the vast majority of the worlds computers. There are many providers to choose from, I chose Entrust. For $20 / year, they will issue me a personal certificate that I can use for S/MIME. How do I know it will work for S/MIME? Simple, it says so, right there in the buy a cert page
Entrust – compliments
Entrust will receive a few rocks in this post, but I will also follow with compliments on their support group and their willingness to help me resolve what was an original fail. For $20 – support costs, they lost money on my sale, but they stood by it and helped me succeed. For that, I write this post so that others will also succeed; hopefully this returns the favor to the kind folks on support line that help me get to success.
Adventures in buying a certificate
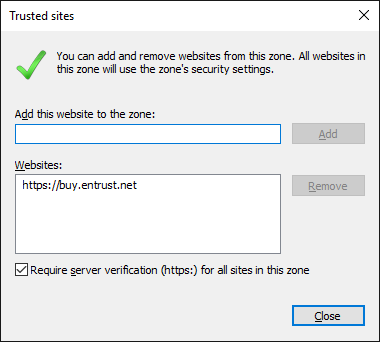
For Entrust, the site to start is https://buy.entrust.net. Visit there, pay your money and out pops a certificate that you can use for S/MIME email. Or so I thought. I am using Windows 10 and I think the site is making assumptions to older versions of Windows and older web browsers.
Mistake #1 – I used Firefox. You must use Internet Explorer. The website doesn’t check this and if you do use Firefox, you will make it through the “pay money” part of the process, but will fail when it comes to the download the purchased certificate part. Turns out that the certificate sale at the end triggers an ActiveX activity to install the certificate into the Windows certificate store and from Firefox, this downloads as the public key part of the certificate only, so you end up with a certificate installed that will not allow you to do anything useful because you don’t have the private key.
Solution A: Contacted Entrust support line, and they issued me a discount code to start over.
Why IE? The website FAQ implies that public key private key pair are generated at Entrust and then they send you the certificate file encrypted with the password you supply during purchase. This isn’t how it works. It is how the website FAQ says it works, but isn’t how it really works. How it works in reality is better, but requires running code client side to do the key generation.
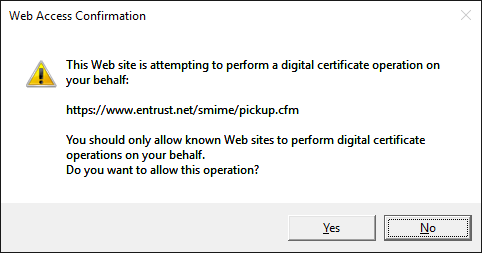
I do not want private key to have ever been in the possession of CA, or anyone except me and neither do they. We want to send them the public key, and have them sign it. This means that the key pair have to be generated on our PC and the public part sent up for signature and then back down to be reassembled and stored as our private key containing certificate which gets written into our system.
To accomplish that, they need ActiveX in the browser or some means to run code client side and with that, they depend on Internet Explorer ability to run ActiveX extensions.
Mistake #2 – ActiveX is rightly blocked by Internet Explorer
I’m on Windows 10. IE security gets better all the time and one thing it has done to get better is turning off the ability for any old website to run ActiveX controls (native code client side). Version of Internet Explorer that ships with Windows 10 does not permit ActiveX for non-trusted sites.
Solution: Temporarily add buy.entrust.net to the list of trusted sites in Internet Explorer.
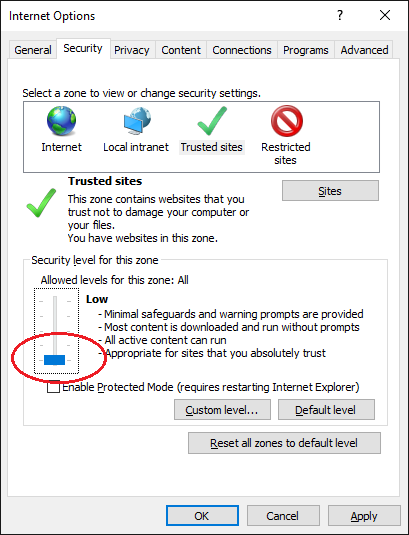
Refresh webpage and think you’ll be good to go. No. Still fails.
Mistake #3 – ActiveX control from Entrust is not properly signed (or not signed at all)
Even with the sales URL added to trusted sites in IE, the browser still refuses to run the ActiveX control because it is not signed. That part by the way is kinda interesting for code from a CA, but save for another day.
Solution: Already willing to lower shields in talking to this website, another step is required to lower shields again to run non-signed ActiveX. This is global for all sites in Trusted Sites, so must be done only temporarily.
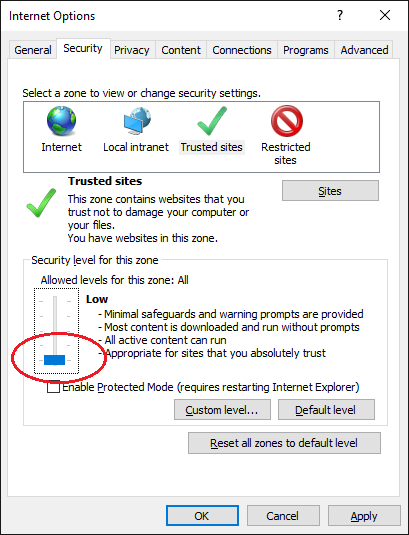
Refresh page and the ActiveX control will run and you can complete the purchase.
It will start with a warning about running the ActiveX control
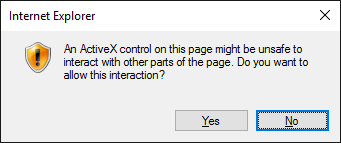
Warning from Windows – an application is wanting to create a private key! Yippie!
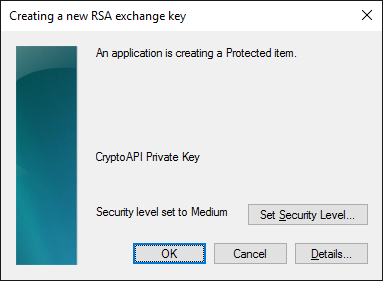
Security level at medium means that you will get prompted to approve access to the private key, but you will not have to enter an access password on each usage. Medium is great, next.
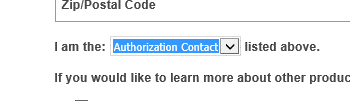
Then you are prompted with a confusing question on what you are for the certificate. You are the authorization contact – the one of highest authority over the cert, king of your own world.
And finally a happy “you’re done” screen — DO NOT CLOSE THE BROWSER!
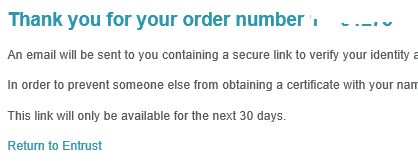
You think you’re done, you’re not. The private key is still in memory inside the ActiveX control inside the browser. Leave it open. Go check email.
Email arrives – has a link to proceed to the next step
Do not click the link – that would just put you back in Firefox or Chome or your other browser that probably isn’t the same browser instance that is running the ActiveX control. Instead, Right mouse button, COPY the link into clipboard.
Go back to the Internet Explorer browser that did the purchase. In theory a new “tab” in that browser would be okay. I did not do that, I pasted into the URL window for the same tab that indicated I had completed purchase. This one I am sure can still see the private key. Paste the URL and press enter to browse to the site.
License agreement
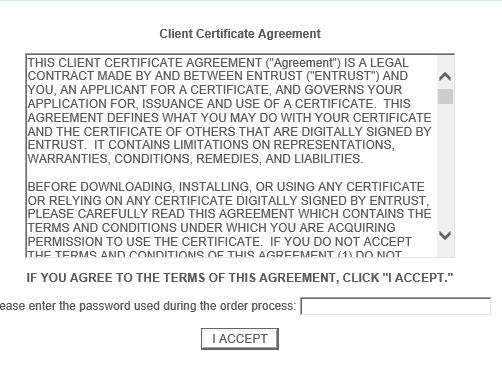
Here, you enter the password that you provided earlier – so that the certificate host side can be downloaded and decrypted.
Happiness – Certificate installation happening, being commanded from the Entrust ActiveX control.
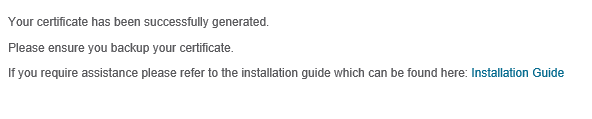
And done. The certificate is installed! Purchase process is complete.
Raise your shields!
The trusted sites addition done during purchasing should be removed and the default security level for sites on the trusted sites should be returned.
Alt-Tools, Options, Security: Remove buy.entrust.net site from trusted sites and raise the security bar for trusted sites back to the default, Medium is where it was before I had to dial it down.
Backup to off computer storage
The certificate is installed onto the computer, but at this moment, that is the ONLY copy. If the computer were to die, access to that certificate will be forever lost. Must back up as a standard part of purchase.
Still in Internet Explorer
Alt-Tools, Options, Security, Content, Certificates
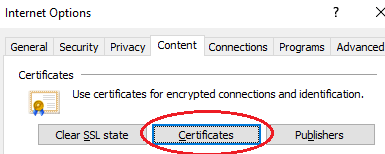
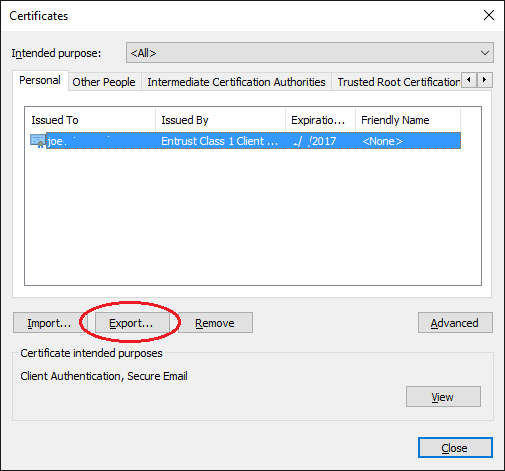
Sends you into the Certificate Export Wizard.
Go through the first screen and on the export screen, tell it YES, include the private key.
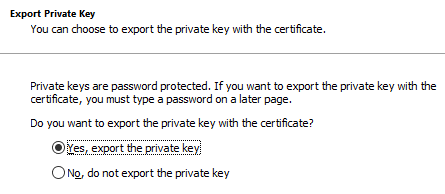
It requires you to add a password, think one up, write it down, export the file. Store on a USB drive, put it with your backups…
And you’re done! Right?
Summary
And you’re done! Right? Answer: You’re not done.
You think you’re done, but you are not. You have successfully purchased and installed a certificate that theoretically can be used for S/MIME, but in reality all you have is a personal certificate that can be used for web browsing. You can now use public/private key crypto via this certificate to mathematically prove your identity to a website. Thankfully this will not happen without your approval, so you can leave this certificate in the Internet Explorer key store and go back to using Firefox who has no vision to it.
As for me, I bought this S/MIME certificate with the goal of sending and receiving encrypted email and so far, it won’t do that. Part 2 of this series will describe how to get Microsoft Outlook to utilize this certificate for S/MIME, link.
Joe Nord
(Originally published Jan 22, 2016)
Pingback: Adventures in S/MIME – Installing certificate for MS Outlook – joenord.com
Pingback: Adventures in S/MIME – Sending encrypted email with MS Outlook – joenord.com
Pingback: Adventures in S/MIME – Certificate Renewal – joenord.com