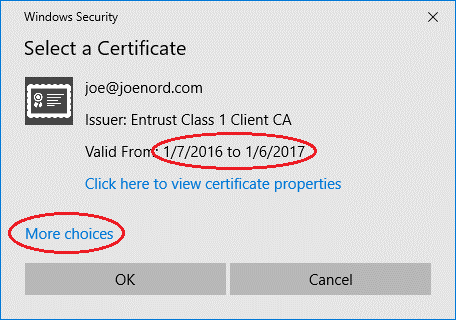
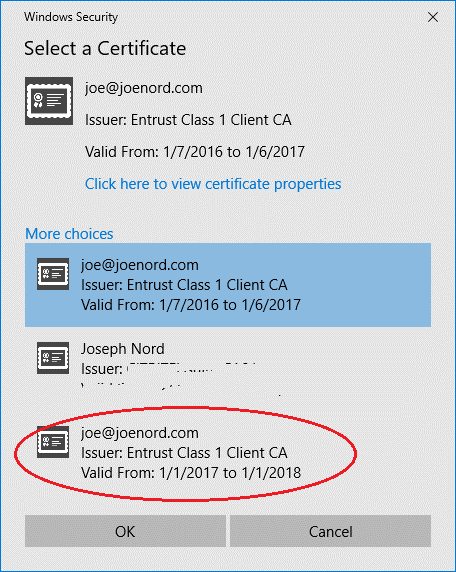
Hurricane approaching, you live on the water with a canal behind the house, does the boat go in the water or stay on the lift? With the experience of hurricane Irma just completed, I can answer this question: Put the boat in the water.
A better answer is “get the boat out of the water, onto a trailer and driving away”. That isn’t possible in all cases, especially for larger boats and I will add that if you think you did well and found a trailer before the storm, you will come home to find the canal is already closed off with neighbors tying off a couple days before storm arrival.
Here in Lighthouse Point (Broward County, Fort Lauderdale, FL), we just experienced hurricane Irma. A pretty good wind here, nothing like the keys, but strong winds at hurricane strength for 6 or more hours. We are a couple thousand feet from ocean, but the barrier island of Hillsboro Mile protects us from the ocean. The Hillsboro inlet is less than 1 mile away. I have two boats of personal study and both made it through the storm with no damage, one in the canal and a smaller boat on side of house on trailer.
First boat, 1995 Mako 22.1-B center console with T-Top which spends most of its time on an “L” lift rated for more than twice its weight.

For smaller hurricanes, I have left boat on lift successfully. Tied boat to the lift and tied lines fore and aft to pilings far away to keep the boat from swaying and potentially twisting the lift in directions where it is not designed to take high stress. This worked, but Irma looked more like a “3” than a “1” – this time I put the boat in the water and it was a good call.
Side note is that, oh I do WISH this lift were a 4 post. L-lift is what I have and as will show later in this post, they don’t fare as well as 4 post. The lateral sway fore and aft breaks “L” lifts and I’ll show a photo of another boat in the city that had this problem with Irma. Look as I could, I could find no example of a boat on 4 post lift failing in this storm – least here where we probably experienced cat 2..3 level damage.
Ropes, line and rode
You’re going to need lots of rope. Find it in the garage, find it in the anchor well, you will never find it at the store unless you thought about this months ahead. Liberate the anchor lines of your primary anchor and all the spares. Turns out the chains are useful. The boat needs to be in a spider pattern in the middle of canal and this will require all of your lines; MORE is better.
Replaced the bow eye and rear tie down cleats
About a year ago, the bow eye on this 20 year old boat was missing. When did it go away? Bottom line, it was “missing” which means it failed and wasn’t as strong as one might think. I had to replace the bow eye and when replaced that on the bow, also replaced the other 2 in the stern. Inspection says that the stainless steel metal had corroded from the inside through, all 3 were weak. The one on front was missing and one of the two from the stern broke during removal. That isn’t supposed to happen! Good news for this storm, I had recently replaced all 3 of the U bolts and all 3 are again strong – I used them as primary attach points for lines from dock.
Spread the load
While the towing U bolts are strong, there is not enough area there to tie things to. A solution is to string ropes through the U bolts and then bring them up to the docking cleats on the top of boat. Instead of that, I built three (3), 3 to 4 foot long ropes out of very heavy 3/4 inch line to attach to the towing eyes. Galvanized shackles on one end attached to the boat and on the other end a large braided polypropylene eye to attach lines to and through. This also has the advantage that everywhere something is connected to the boat, it is underwater during storm, which should keep it cool and help lines survive periods of high load. It has disadvantage that if the shackle or U bolt fails, the lines will go free with no top side cleat to try to hold on.
On the front, the trailer eye is hard to get to, so I used a large hook with spring lock and here, used metal eye on the water end – connect lines using shackles, as exist on anchor lines – anchor removed. On some, used anchor lines on shore with chain in a loop around piling – that worked very well.

The canal faces east – there are 2 lines to shore on both the front and the rear of the boat and for bonus points, a pair of north / south (side) lines to keep the boat from getting too close to the shore. If all goes as planned, these side lines never take a load. Also, with Irma, weather forecast said strongest winds would be from the south, so added an extra set of lines from the boat right rear U bolt to a separate piling on the shore. Both lines would have to fail to send the boat wondering.
When get done, the boat looks like this in the canal. Most of the front line attachments are not visible – they are all underwater.

A nice photo, observe it also has a different boat on a lift to the left and a jet ski on a floating dock on the far side. BOTH also survived the storm though the floating dock was doing a backward wheelie at highest part of storm tide with its nose held under the seawall.

Most of the lines were sent from boat to shore around piling and then back to the boat. This made it possible to adjust line length from the boat to all shore attach points. I note that it also means that when you get done adjusting all the lines you have to SWIM to shore! I have seen people make mistake of trying to keep the boat off the dock, but close enough to make the jump. No! put the boat in the middle and swim in.
To do better, each line from shore to boat should be distinct line so that one failure would not allow the doubled line to unwind. It didn’t matter, everything held. Also, advice from many says that the lines need to be tied DOWN to the dock so they do not get pulled above the piling. Used small ropes and bowline knots to keep the lines near bottom of the piling, allowing the lines to slide but keeping them held down on the pilings. This worked out to be extra prep with no return because the water never got high enough for it to matter.
As predicted on the news, the water did get high though. Not like a direct hit, keys style high, but higher than I have ever seen it before at this location. It got about 6 inches above the level in the photo below. The boat was not troubled and found the windy day to be similar to a pretty ordinary day in the ocean. There was lots of mess to clean up, but no damage.

My immediate neighbors didn’t have any issues. Boats on lifts, boats in water, all fine. Further down the canal, there was damage. Below is a picture of a large sailboat that was tied off the dock, but not far enough to allow the lines to stretch. Both boat and dock suffered damage – a serious eroding of
piling can be seen in this picture.

A few canals away, was an example of a boat on an L-lift where the lift failed. It looks like lateral movement on the “L” lift caused 1/2 of the lift to fail, tossing the boat into the water during the storm. Boat survived, with damage. In this case, the boat from L lift was at end of canal and tying up “to the street” where I stood taking this picture would have been pretty easy. Majority of wind would have blown “away” making for a pretty good case for “put it in the water”. To note though, the trees on shore were blown down so it would have taken some work to find a good place to tie on.

Leaving boats on floating lifts was also a losing proposition. When the water rises higher than the floating lift can ascend, the boat takes a dip. Answer: Put the small boat on a trailer or put the boat in the water. Observe that the floating dock rose, damaged the dock, then the water receded, with the floating lift stuck to the dock, putting the back end of the boat into the water.

I have a Boston Whaler very similar to the above but a bit smaller, that one looks like 17, mine 15. Kept on trailer on side of house, tied to 3 concrete deadmen installed about 10 years ago with chains that just stay there waiting for the rare storm. The anchors here go down into ground about 4 feet with a few bags of concrete each. In addition to tying the trailer to the ground, we tied the boat to the trailer and filled the boat anchor well with water to make it heavy. The boat weathered the storm with no issues. The fence in front of it blew down. I tied the fence to the boat during storm to keep it from getting loose.

No matter what happened to my little boats, it could be worse. Less than a mile from here is the Hillsboro Inlet and there are some beautiful homes in that stretch of real estate including this one, just a couple houses from the inlet.
This is/was a beautiful monstrous yacht, which did not survive. I hear the back end came loose during the storm and banged against pilings, and she sank. That is a bad day. On the front not visible in this picture is anchor chain tied up into the yard around a very large large silver palm tree, that held. The back end just couldn’t have a big enough anchor? Big sail, hard to win?

Summary
With the experience of hurricane Irma, I observe a few things
- Boats in canals do better than boats on lifts in strong storms
- Boats on trailers tied to something heavy can survive lots of weather
- 4 post lifts do better than L lifts
- Floating boat docks are not a really good place to be
Ideally, I’d invest in a trailer and put the boat on the trailer for a storm. Would then need a place to store the trailer and would also have to get out “early” to avoid the nest of boats strung across the canal. Trailer is the best answer – and a truck to tow it away from storm. Baring that, for category 1, the L lift with bracing will be fine. For category 3, my ship plan says put the boat in the water. For category 4 like the Florida Keys just experienced 100 miles south of here, well you’re screwed either way and I’m not sure anything would help.
Joe Nord
4 comments
Comment from: Harry Alverio Visitor
Hi In Puerto Rico , a lot of boats survived in the cannals during hurricane Maria . They were tied the same way. Those left in the marina got hurt the most , hitting pillings and other boats. I trully belive that if you cannot take the boat out of the water try to move it to channels or mangrove protected areas. This is my 2 cents!
03/28/18 @ 12:26 am
Comment from: joe Member
Thank you for the comment Harry. With Maria, Puerto Rico went through some real mess and I wish you safety and happiness.
05/24/18 @ 01:56 pm
Comment from: Shawn Visitor
Hey Joe,
I am moving to Florida shortly. I will also be living on a canal way. This was a very helpful read. I have been worried sick about what to do with my boat. No one really talks about boats on canal ways during hurricanes.
Just curious, if everyone is tying up all up and down the canal, what happens when one boat isn’t secured properly and starts making its way up the canal and hitting other boats? do you worry about that?
sorry for commenting so much later than your post. just finally came across this!
04/18/19 @ 03:52 pm
Comment from: joe Member
Hi Shawn, welcome to the neighborhood.
> Just curious, if everyone is tying up all up and down the canal, what happens when one boat isn’t secured
> properly and starts making its way up the canal and hitting other boats? do you worry about that? Everyone worries about that, and we worry about it before the storm. If a boat is in the canal and for some odd reason is not making its way to the middle of like all the other boats, look for the neighbors to knock on the owners door and offer encouragement and assistance. Common also for people to take dinghies up/down canal before the storm and inspect the rope and knots of everyone up-wind.
Originally posted Sept 30 2017